How to Use the Attack Surface Page?
RHL ASM Platform is designed to manage attack surfaces by detecting all assets associated with your organization to protect them from external threats. By utilizing the platform, you can effectively identify security vulnerabilities and gain insights into areas that pose risks. Through continuous analysis, the platform can detect changes in the attack surface, helping reduce the risk of cyberattacks.
The Attack Surface module is divided into the following sections:
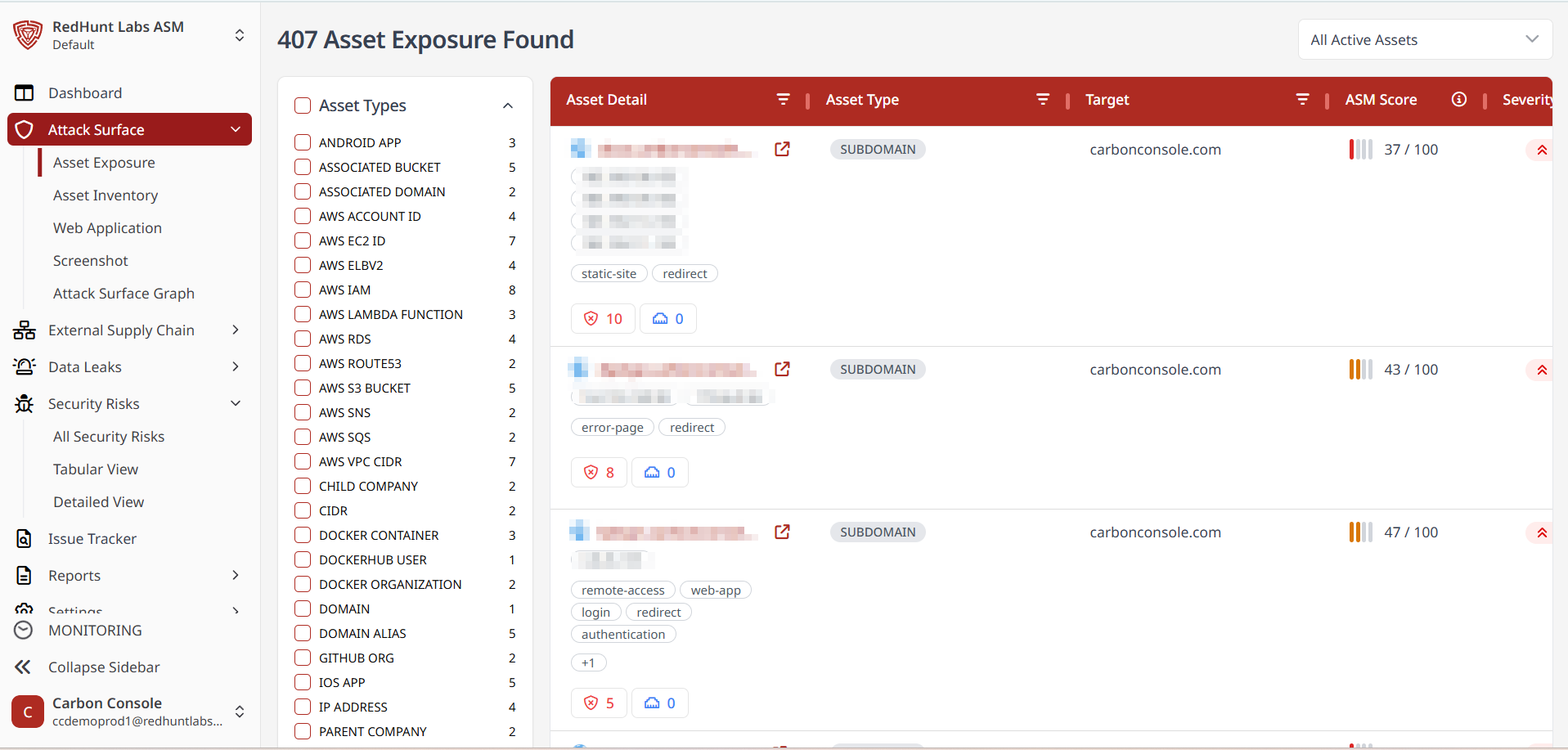
Asset Exposure
- The Asset Exposure section displays a list of all identified assets, along with details such as URL, asset type, asset tag, potential risks, cloud classification, and First Seen and Last Seen dates.
- To simplify navigation through a large number of assets, you can filter the data by asset type, tags, and status.
- Filtering options include:
- Asset Types and Tags: Click on a specific asset type or tag to view filtered results.
- Asset Status:
- All Active Assets Since: Total number of active assets discovered since the last scan.
- New Assets Since: Assets newly found in recent scans.
- Assets Not Found Since: Inactive assets no longer found in the latest scans.
- You can also apply time-based filters to view assets found within the last 7 days, 1 month, 6 months, 1 year, or use custom date ranges.
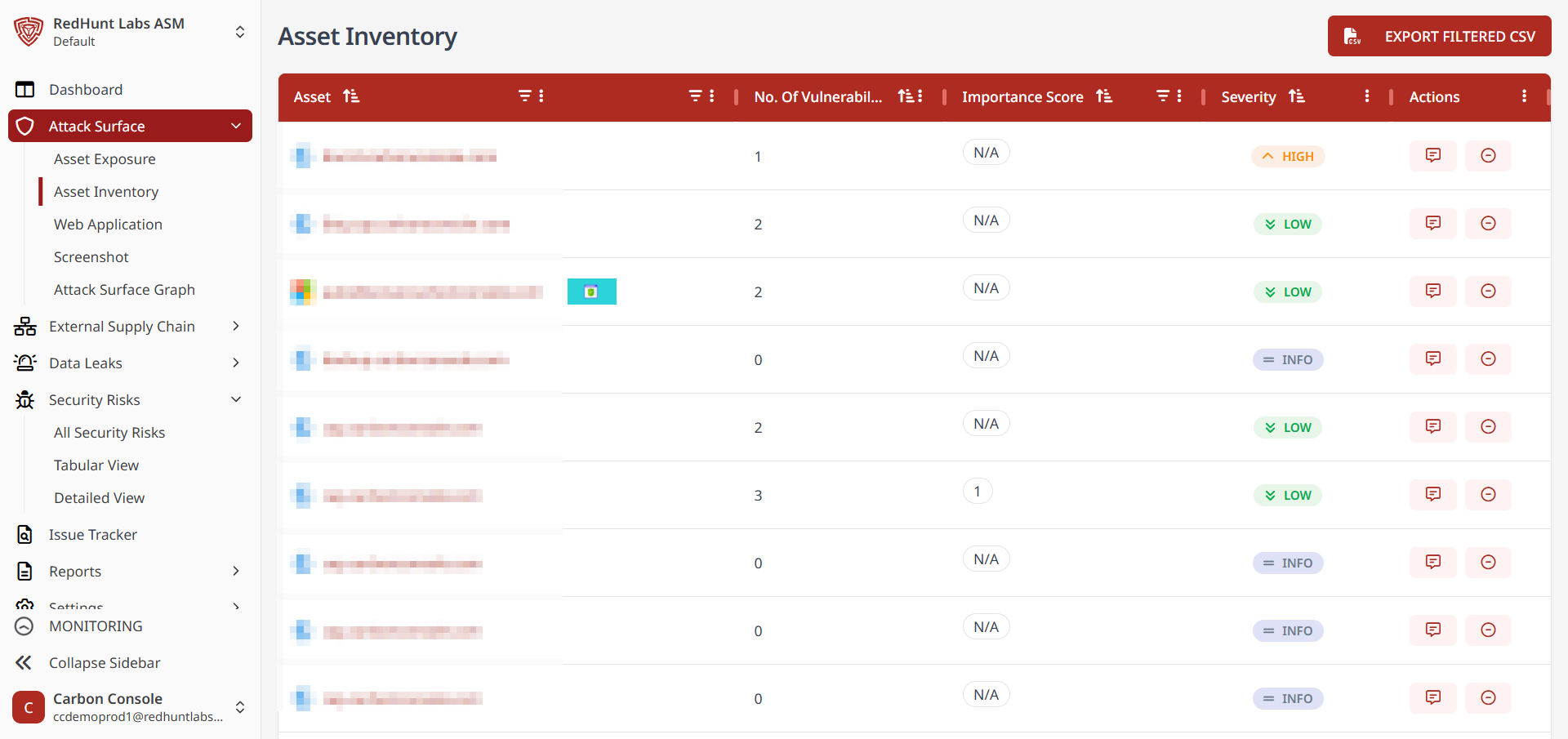
Asset Inventory
- The Asset Inventory section displays all identified assets in a tabular format.
- Each asset includes information such as asset type, open ports, tags, technologies used, number of vulnerabilities, severity level, and first and last seen dates.
- Filtering options include:
- By Input: Enter asset name (URL), port number, or technology in the respective fields.
- By Dropdown: Select asset type or tag from the dropdown menus.
Actions:
- To add tags to selected assets, go to the Actions tab within the Asset Inventory section, enter the desired tag name, and click Add. This allows you to create and assign custom tags.
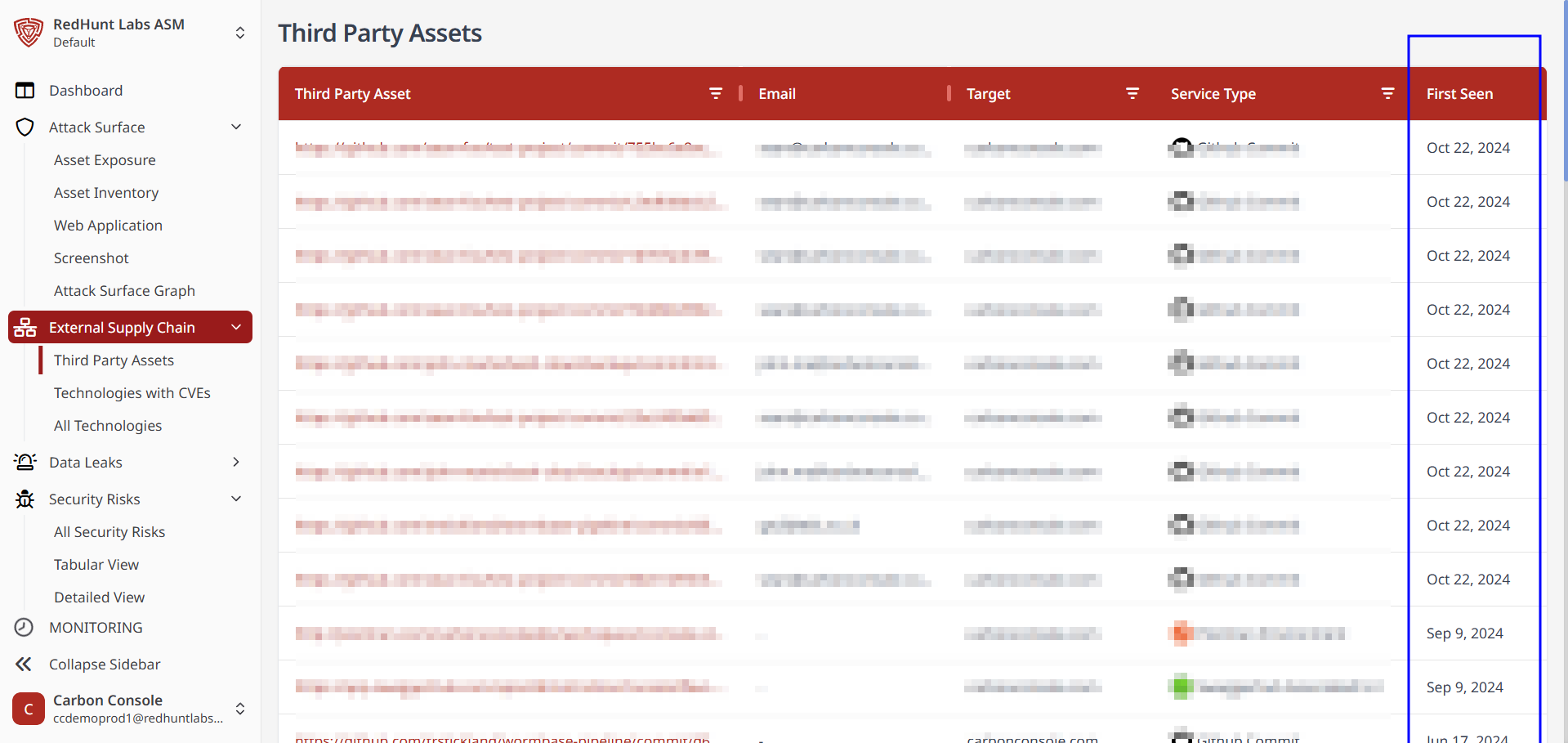
Third-Party Assets
Third‑party assets refer to services or tools used by an organization that are sourced from external vendors, whether or not a formal agreement exists. Examples include cloud-based software services, web hosting, project management tools, CRM systems, and communication platforms.
- All discovered third-party assets are listed in this module.
- Information displayed includes:
- Asset URL and platform used
- First Seen date
- Last Seen date
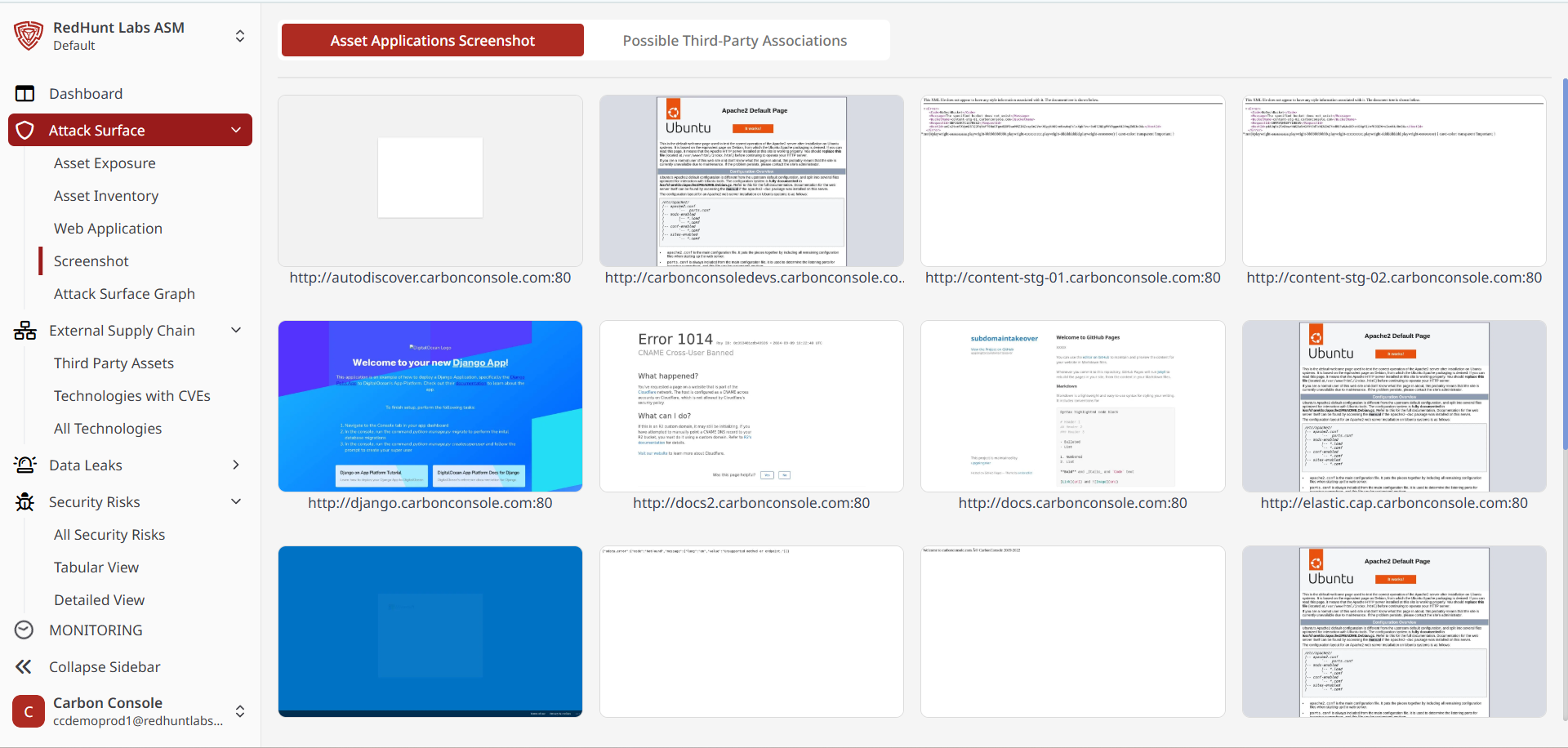
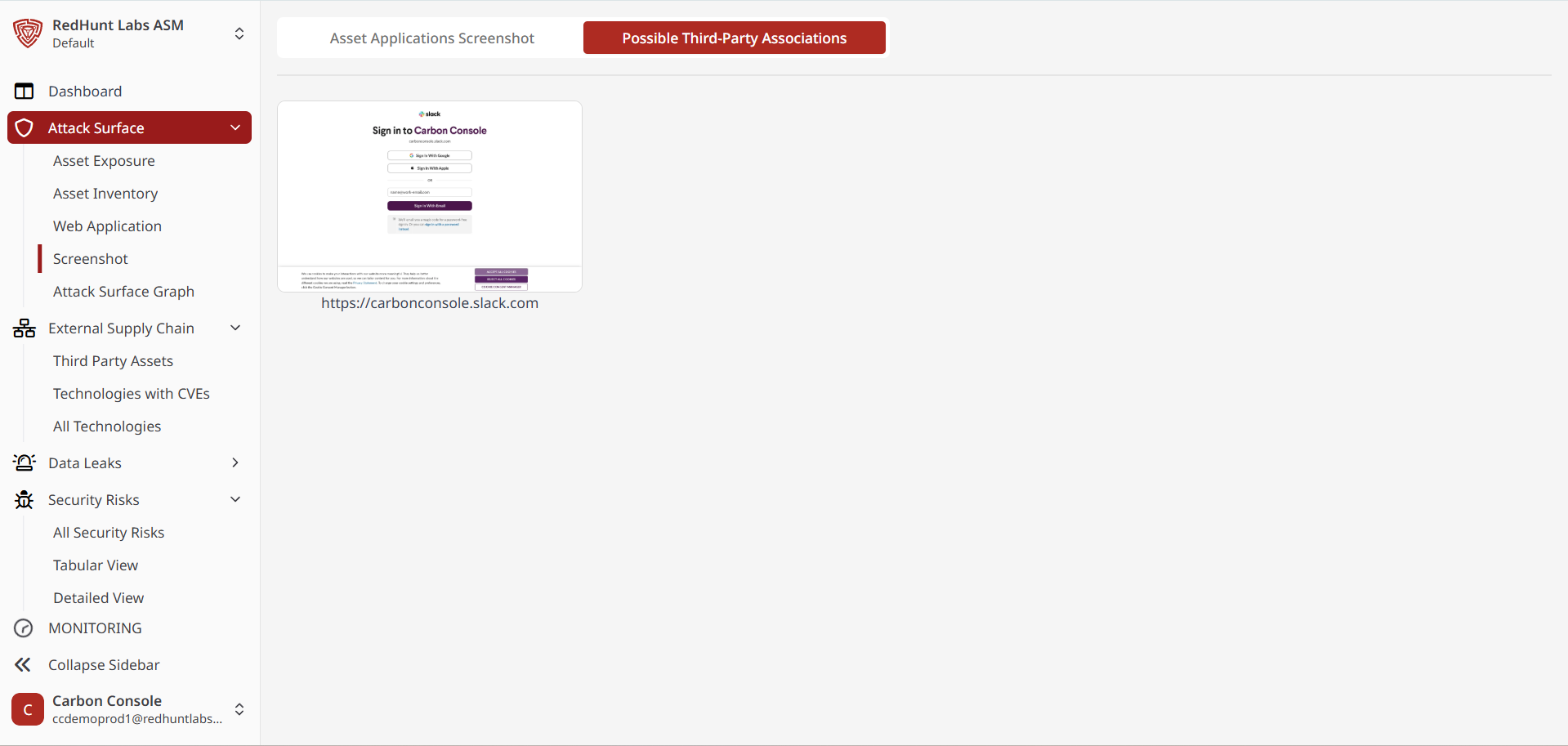
Screenshots
Screenshots provide visual captures of unexpected responses or content detected across various ports of discovered assets. This module is divided into two tabs:
- Asset Application Screenshots: Displays response screens of the assets belonging to your organization.
- Possible Third‑Party Associations: Displays screenshots of third‑party assets discovered during scans.