How to Use Data Leaks Page?
A data leak (also known as a data breach) refers to an incident where confidential or sensitive information is accessed, viewed, stolen, or released without authorization. Data leaks can occur in various forms—both digital and physical—and can affect individuals, organizations, or government entities.
RHL ASM Platform offers a data leak detection feature that thoroughly scans your organization's IT environment to identify instances of exposed sensitive data. Through continuous scans and identification of data exposure, this feature helps enhance your organization’s data security.
To learn more about data leaks, see: What is a Data Leak?
What Are Signature Filters and How to Apply Them?
- The platform provides a set of signature filters, which are predefined categories used to sort data leaks.
- These filters are based on the most commonly detected types of data leaks and are located on the left-hand side of the Data Leaks screen.
- By selecting a specific filter, you can view all associated data leaks.
- Simply click the desired signature filter to display relevant data leak instances.
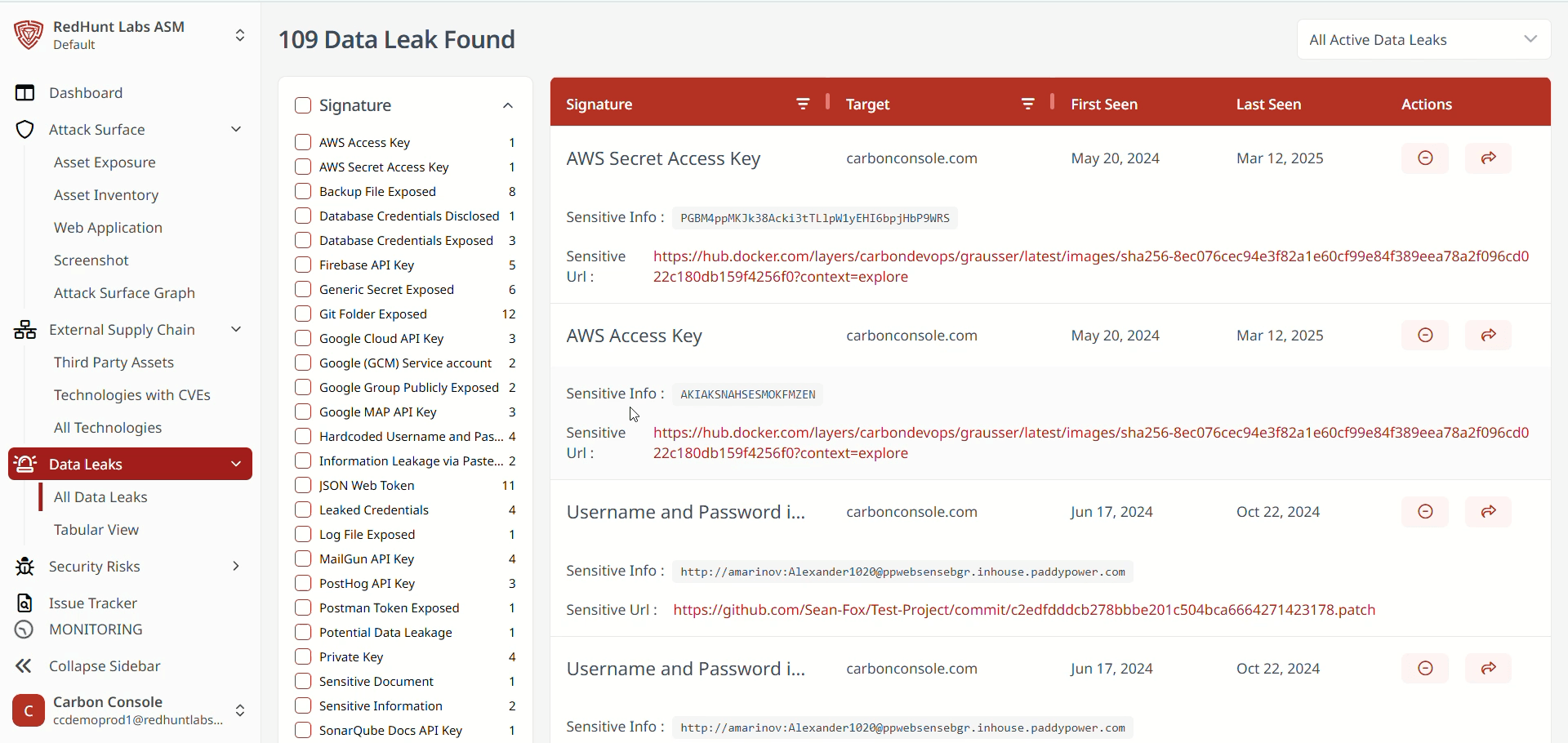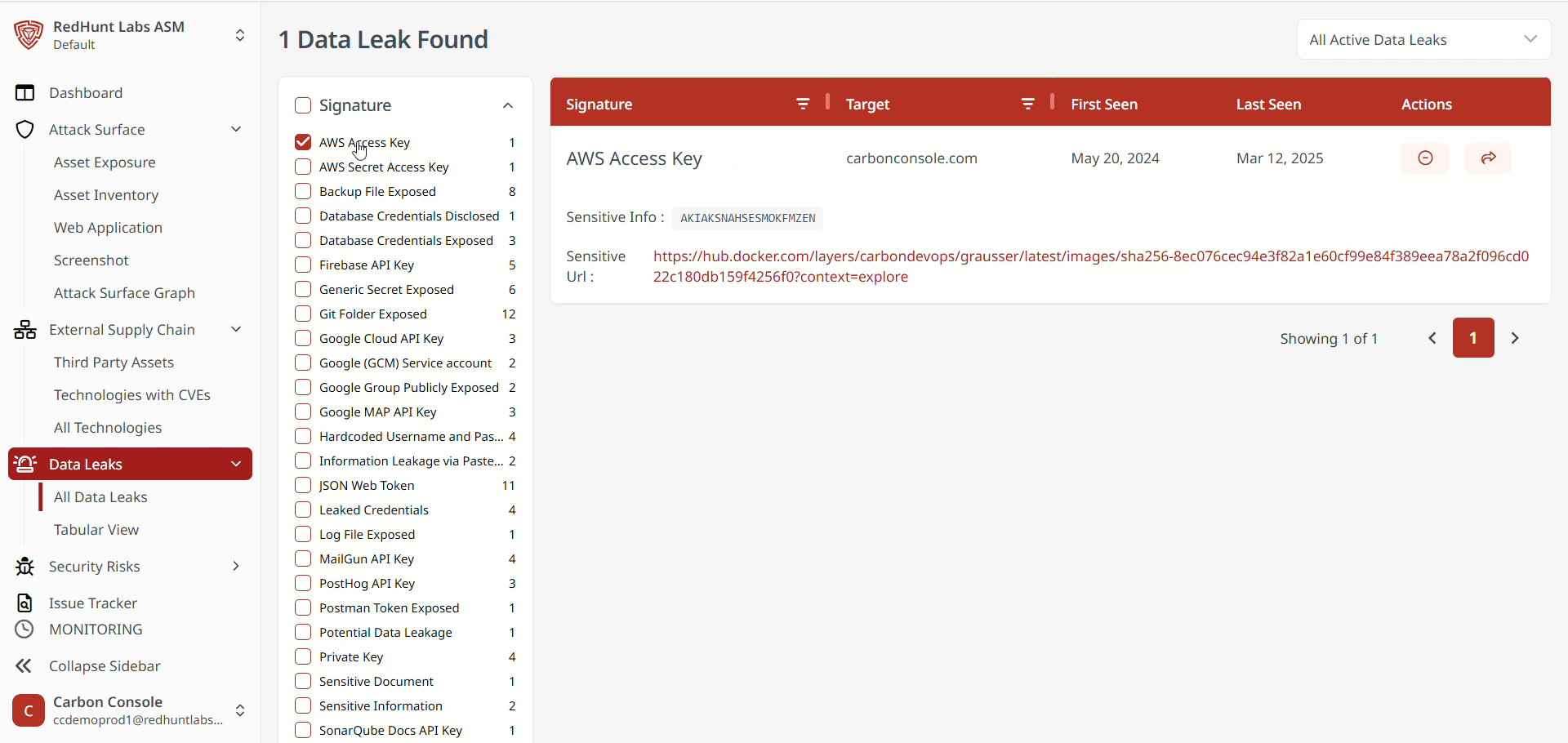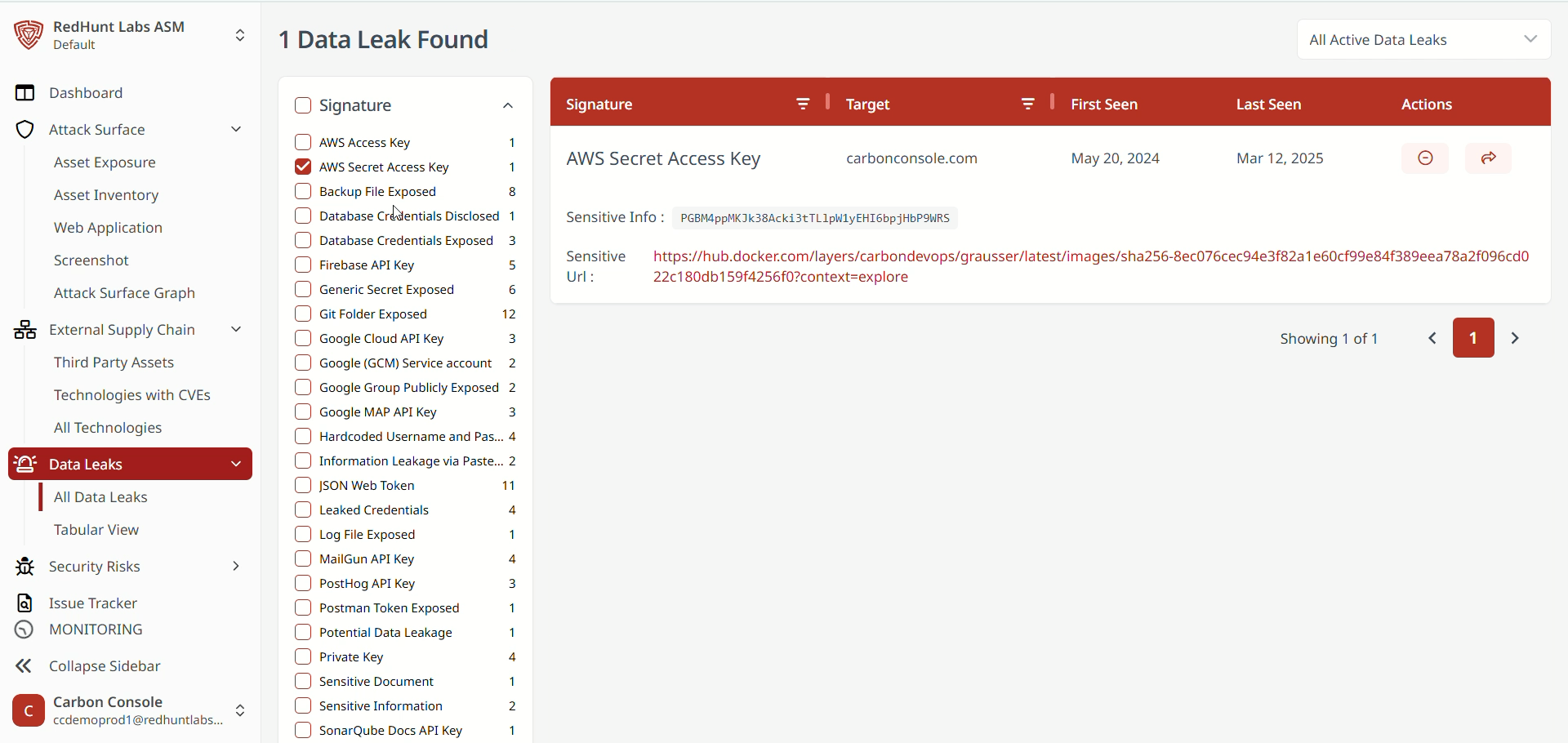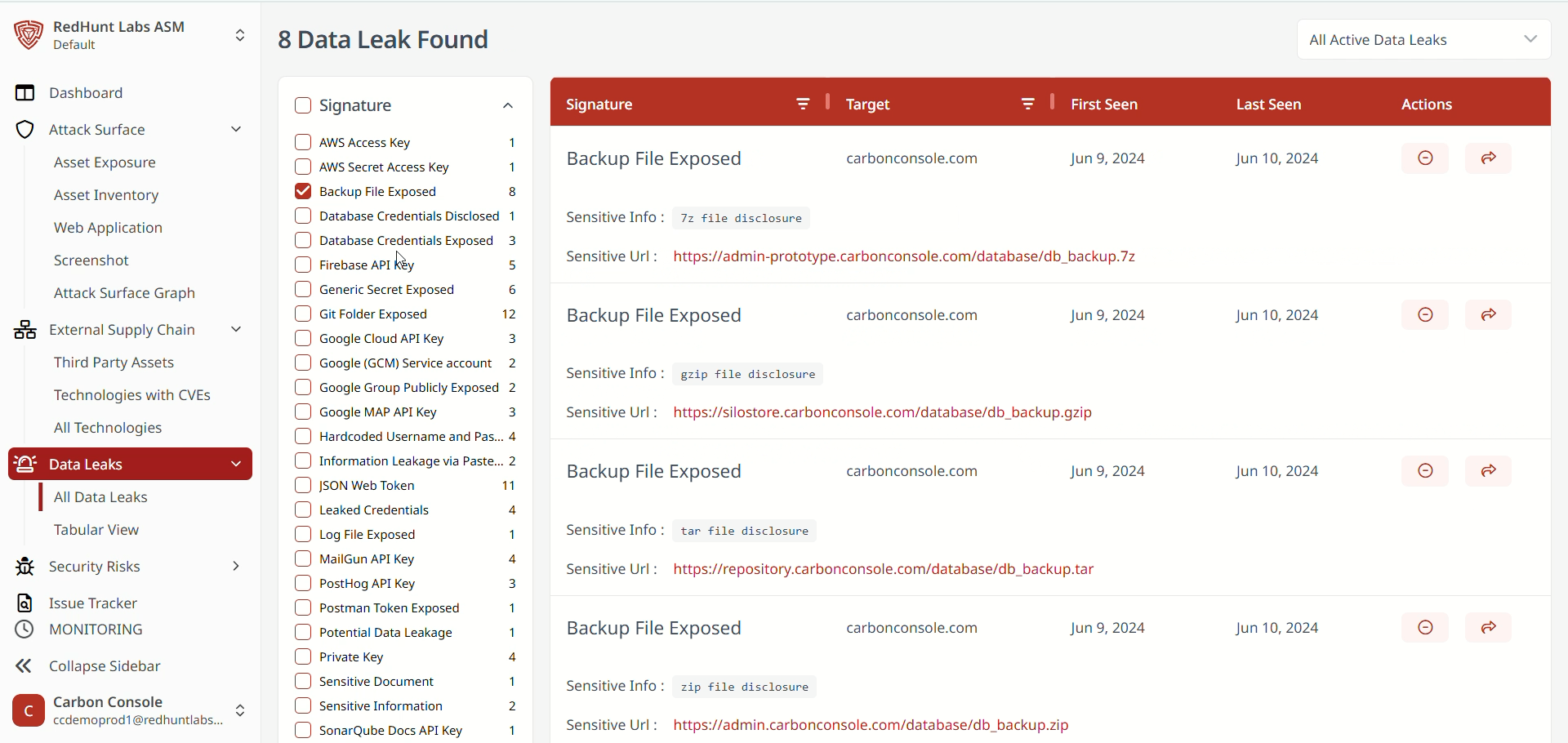
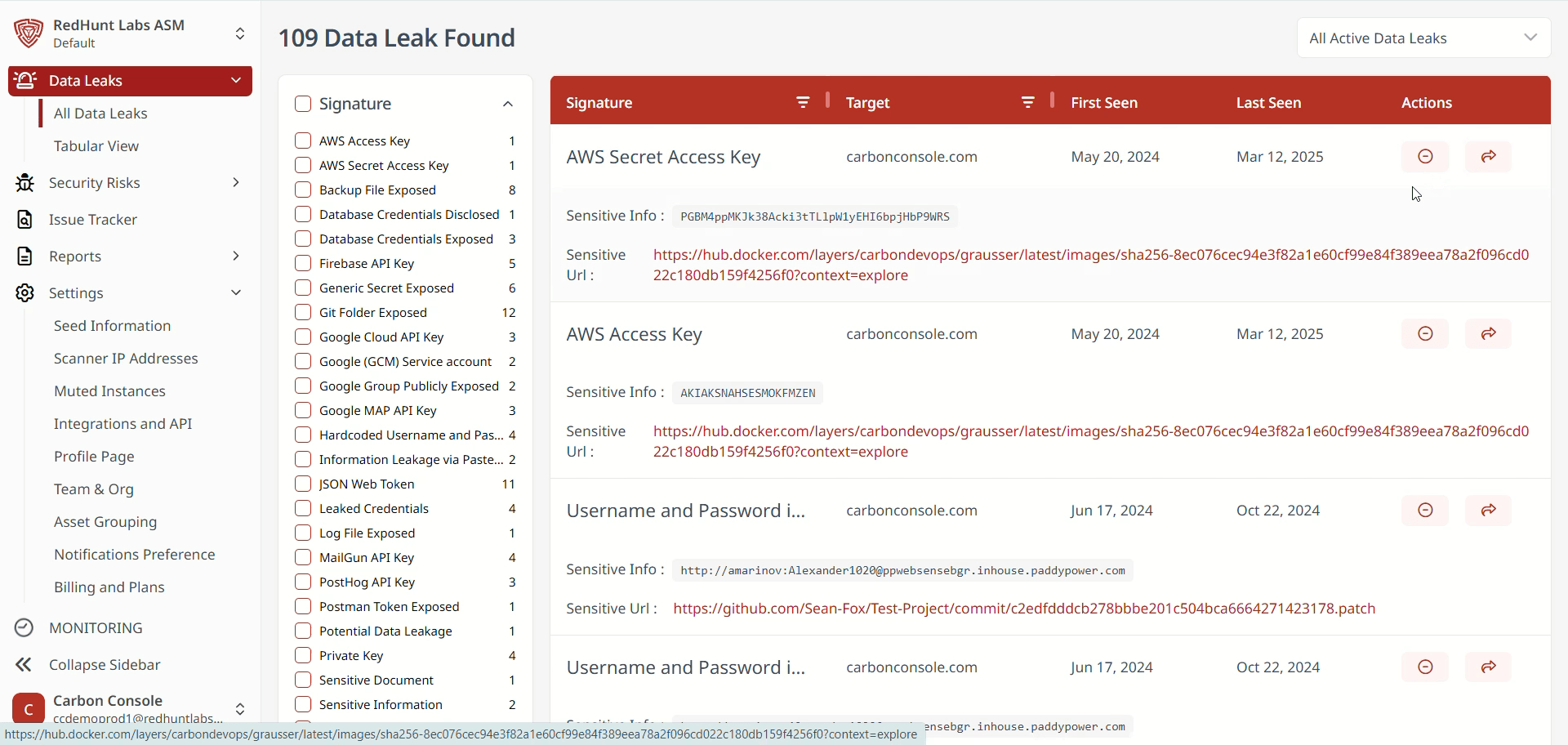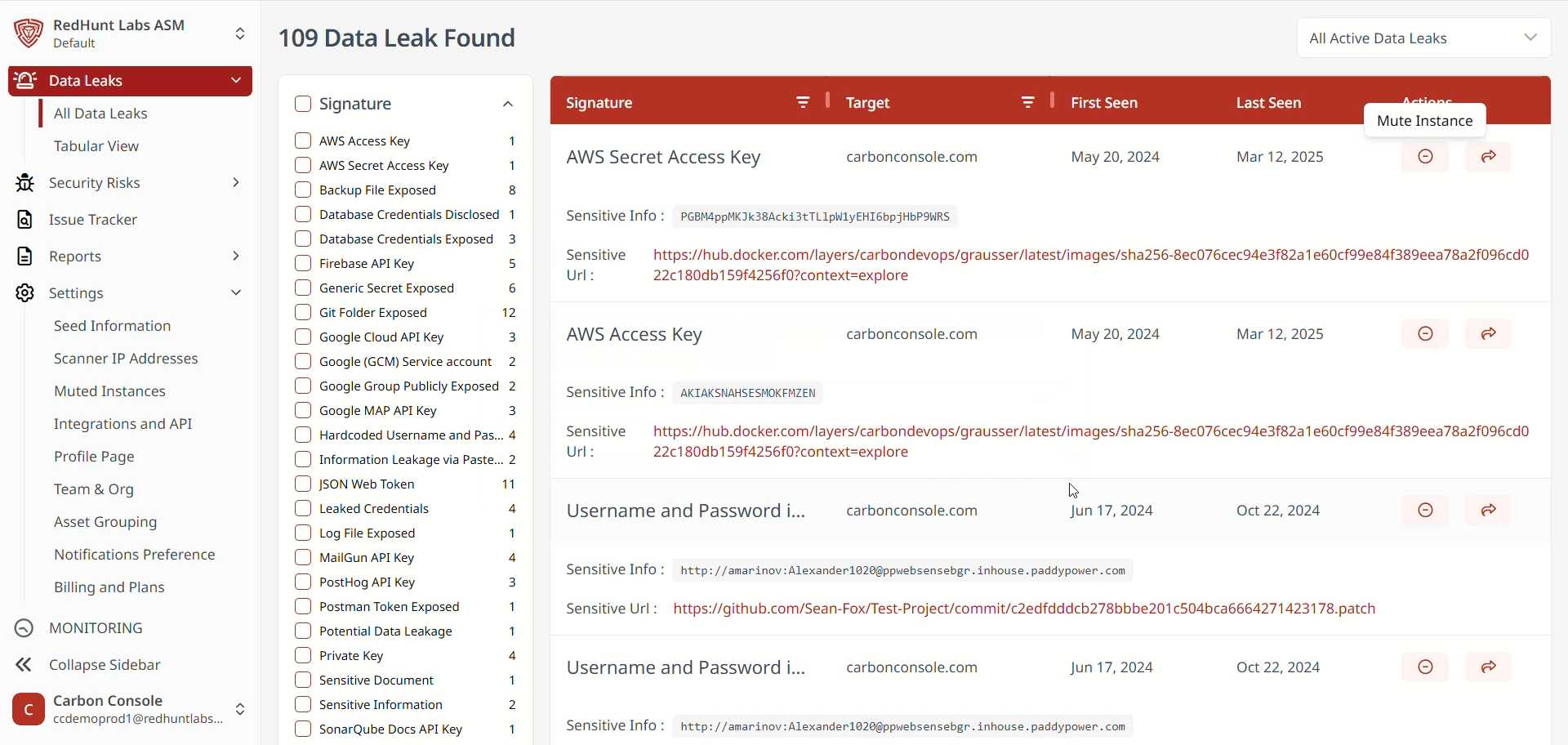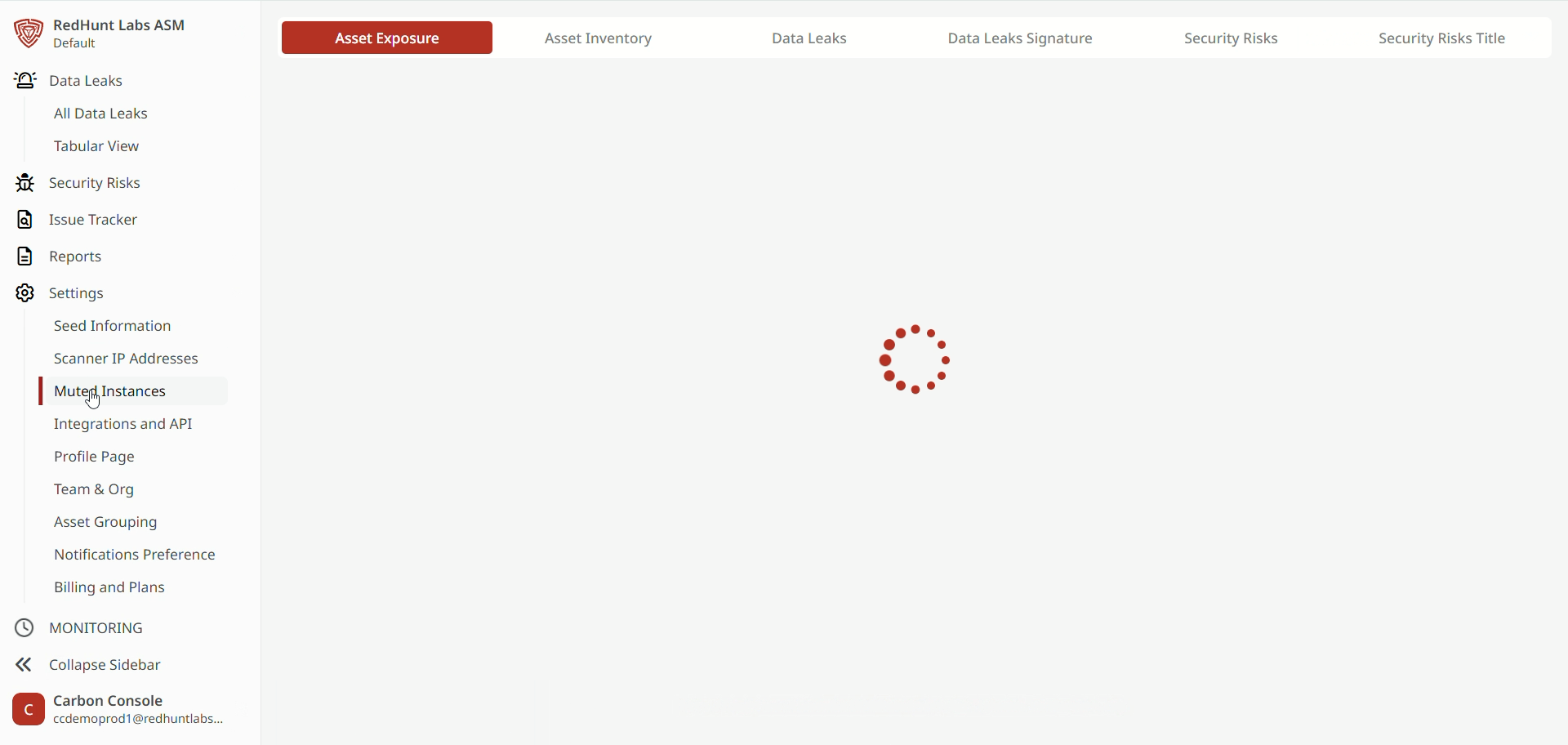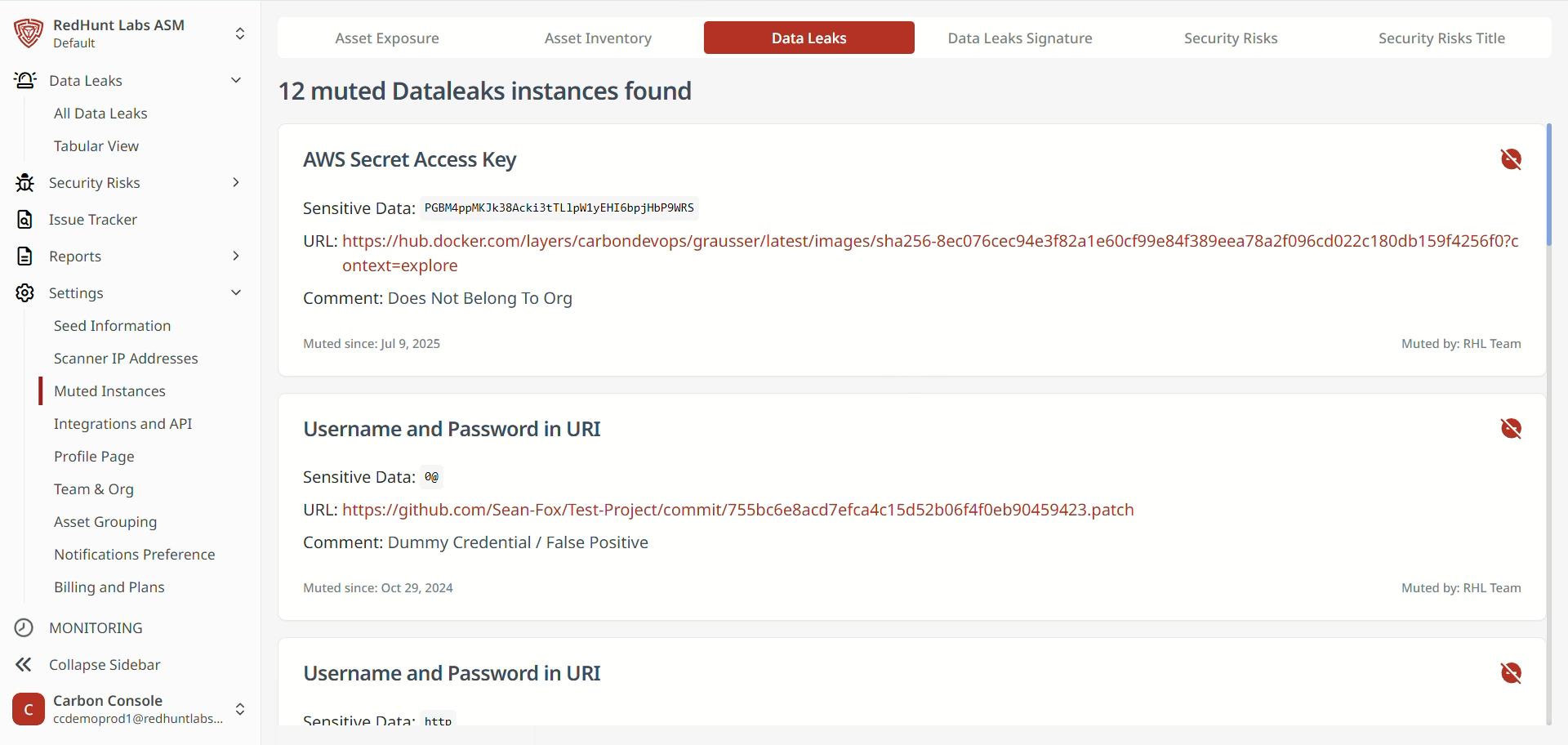
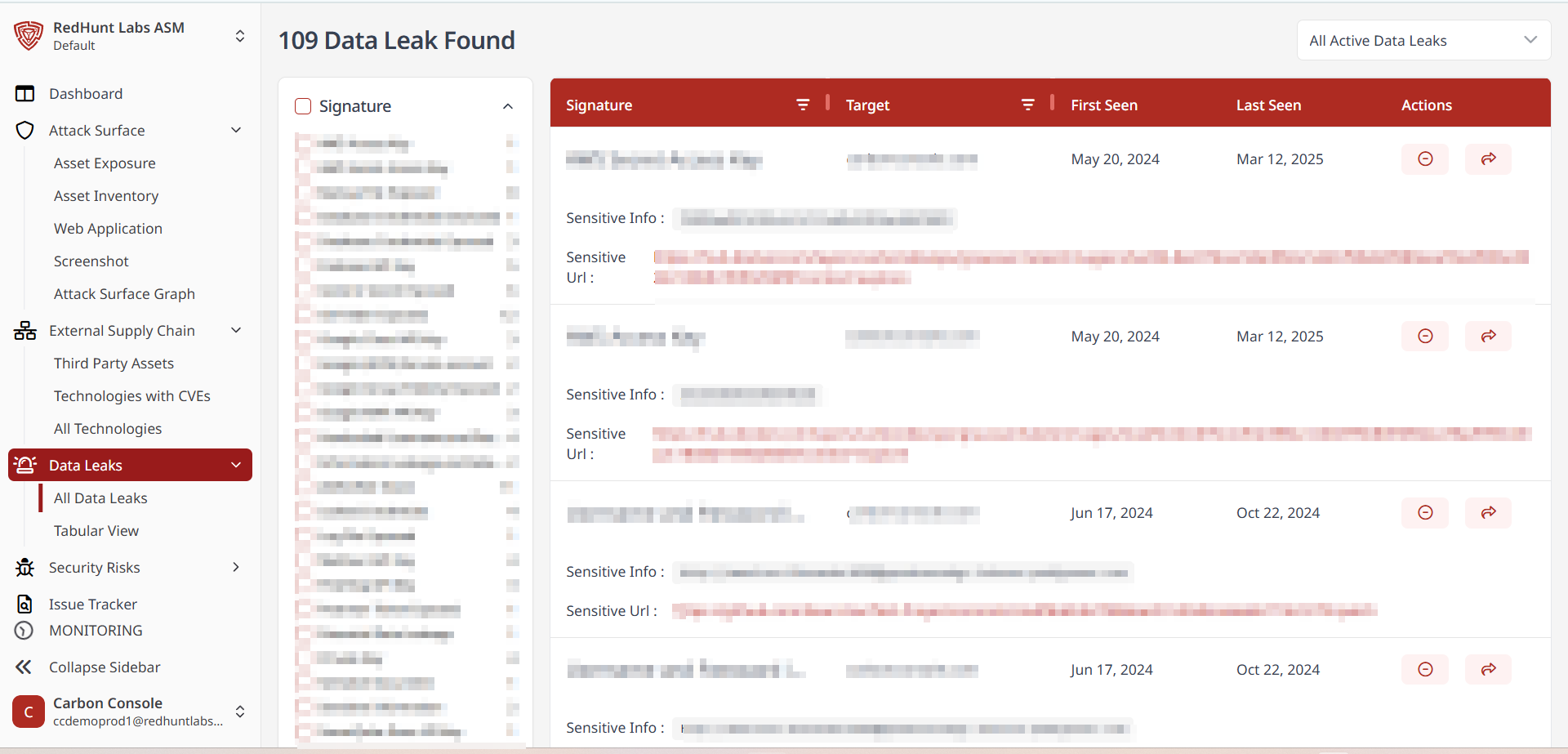
Features Available Under the ‘All Data Leaks’ Layout
- The All Data Leaks layout displays data leak instances in a list format.
- You can sort the information using filters based on instance category and scan status.
- Additionally, you can:
- Mute a specific instance (available only in list view).
- View the platform that exposed the data.
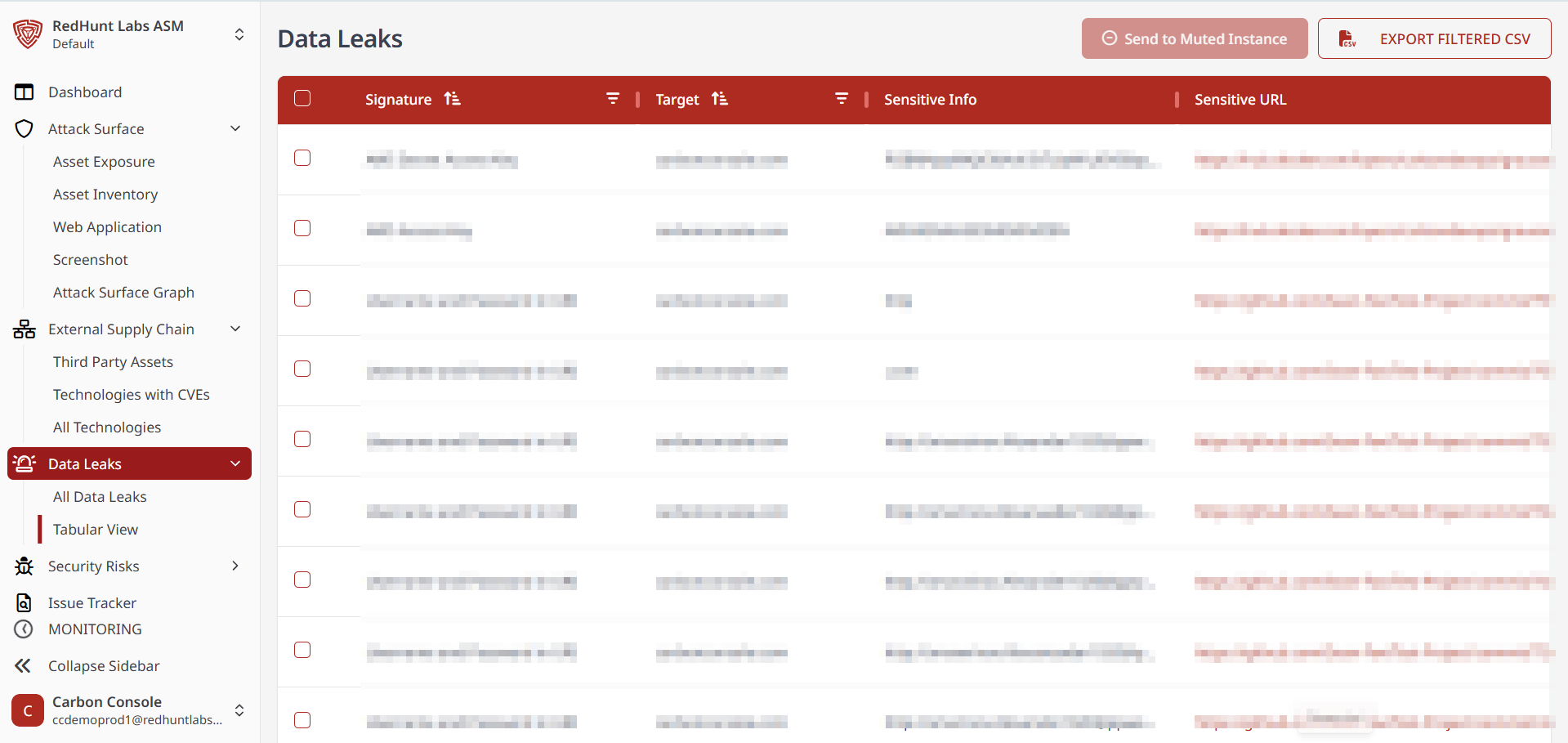
Features Available Under the ‘Tabular View’ Layout
- The Tabular View presents data leak instances in a row-and-column format for a more analyst-friendly interface.
- Both the list and table layouts contain the same information.
- You can filter data based on asset names or signatures.
How to Mute a Data Leak Instance?
- Navigate to the List layout under the Data Leaks section.
- Click the mute icon at the right end of the instance you wish to mute.
- A Mute Instance pop-up will appear, allowing you to:
- Select a reason for muting.
- Access a link to the settings page where muted instances can be deleted (to unmute them).
- Click OK to confirm.
- A success notification will appear.
- Once muted, the instance will no longer trigger notifications in future scans.