How to Use the Security Risk Page?
The RHL ASM Platform is designed to identify security vulnerabilities across your organization's assets. Prompt remediation of these risks is crucial, as they can lead to data breaches and other cyber threats. To aid in swift detection, the platform offers a comprehensive set of predefined security checks.
Security risk instances are categorized and listed under the Security Risks module based on predefined criteria, enabling streamlined risk management.
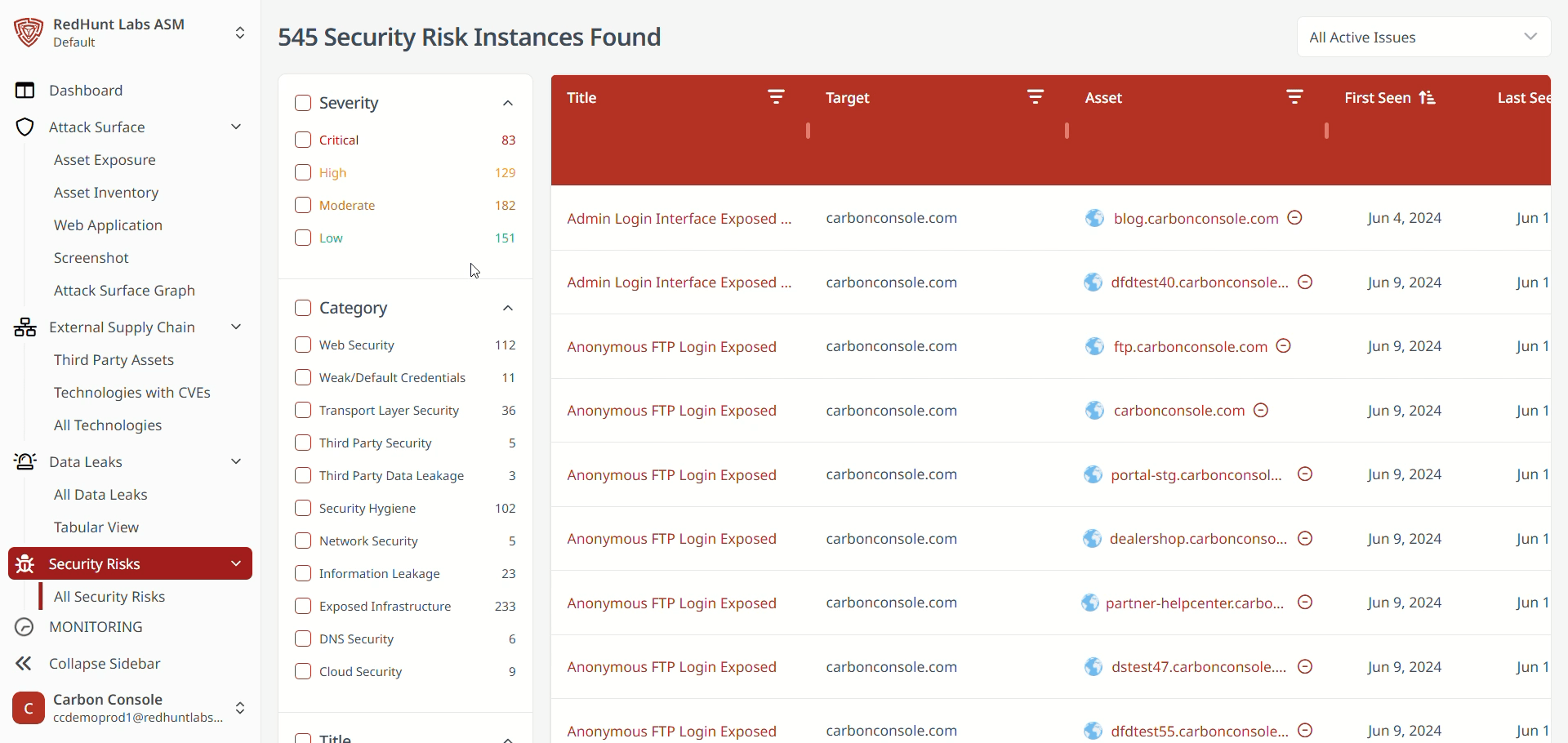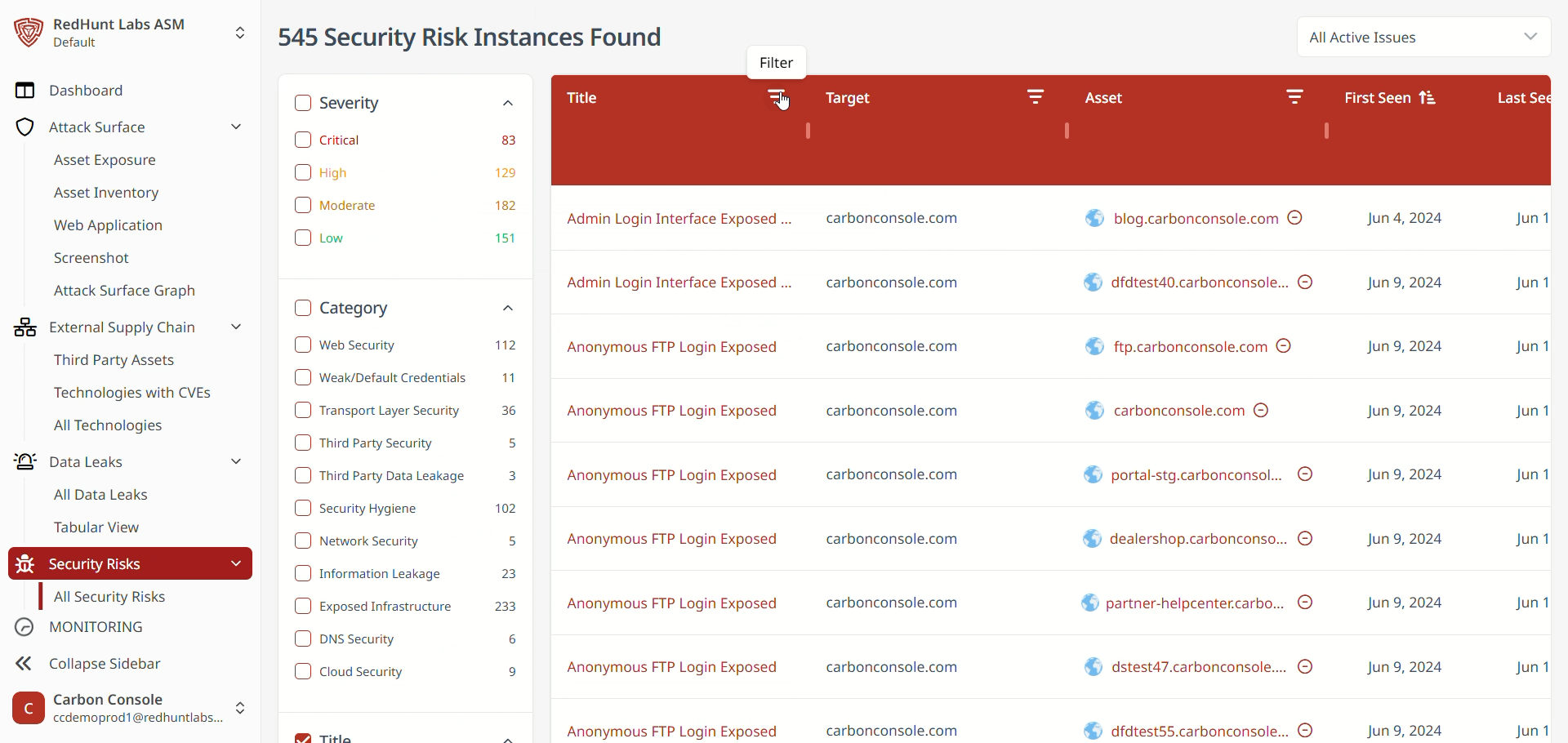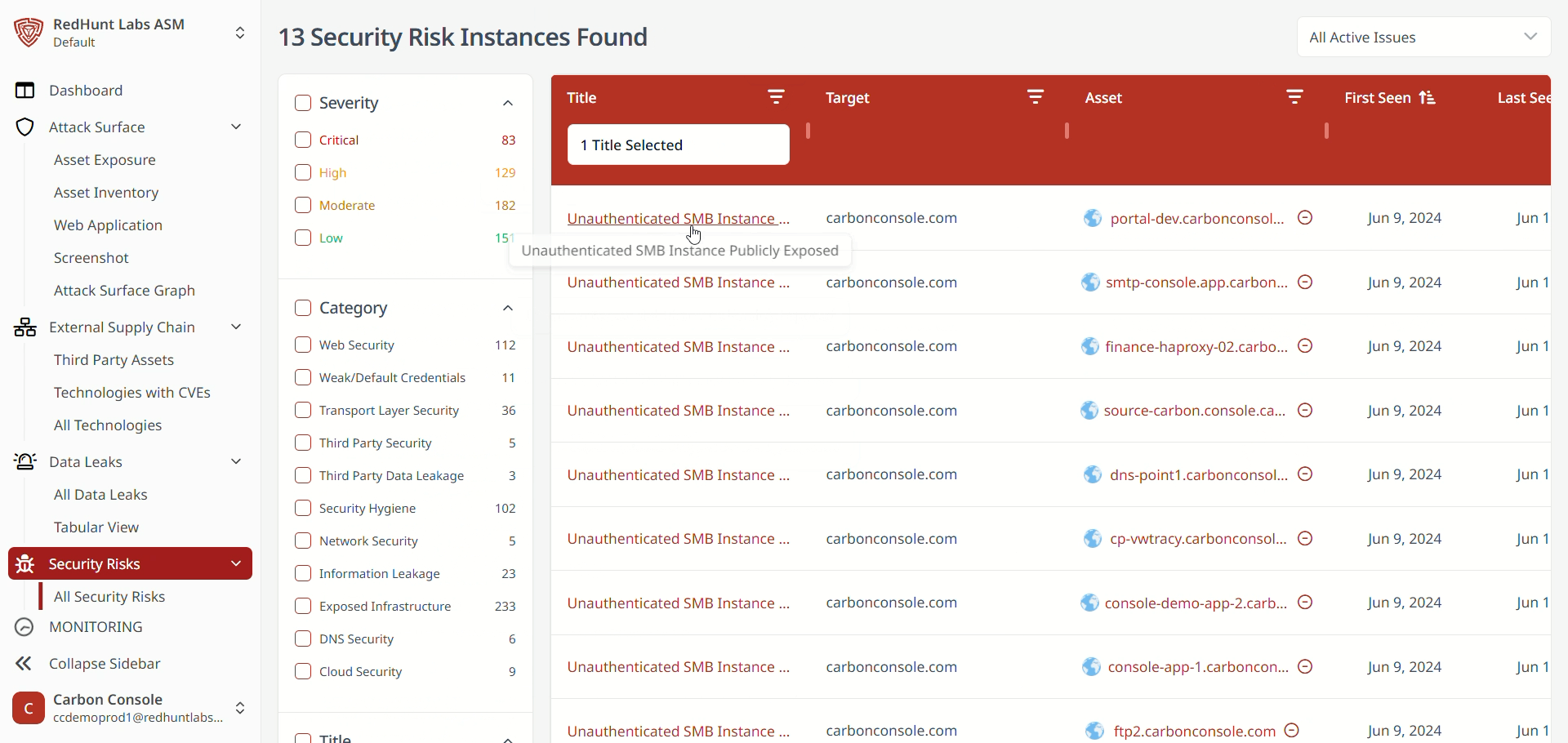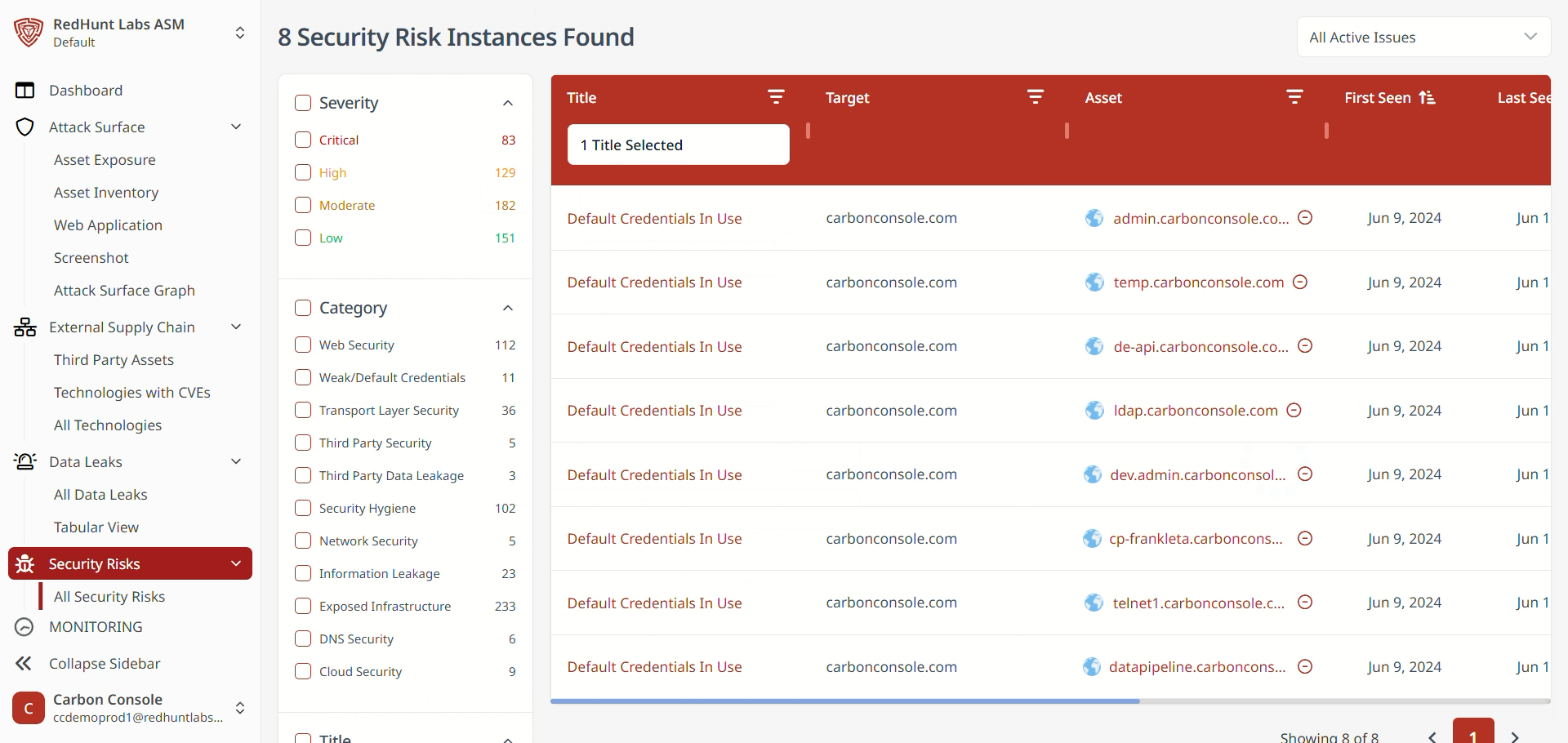
Features Available Under the ‘All Security Risks’ View
- Security risk instances are displayed in a list format.
- You can filter the displayed information by severity, category, and scan status.
- Options include:
- Mute an Instance (available only in the list view).
- Send to Issue Tracker directly from the interface.
- For a detailed overview, click on the category name of an instance. This navigates to the corresponding category under the Detailed View sub-module.
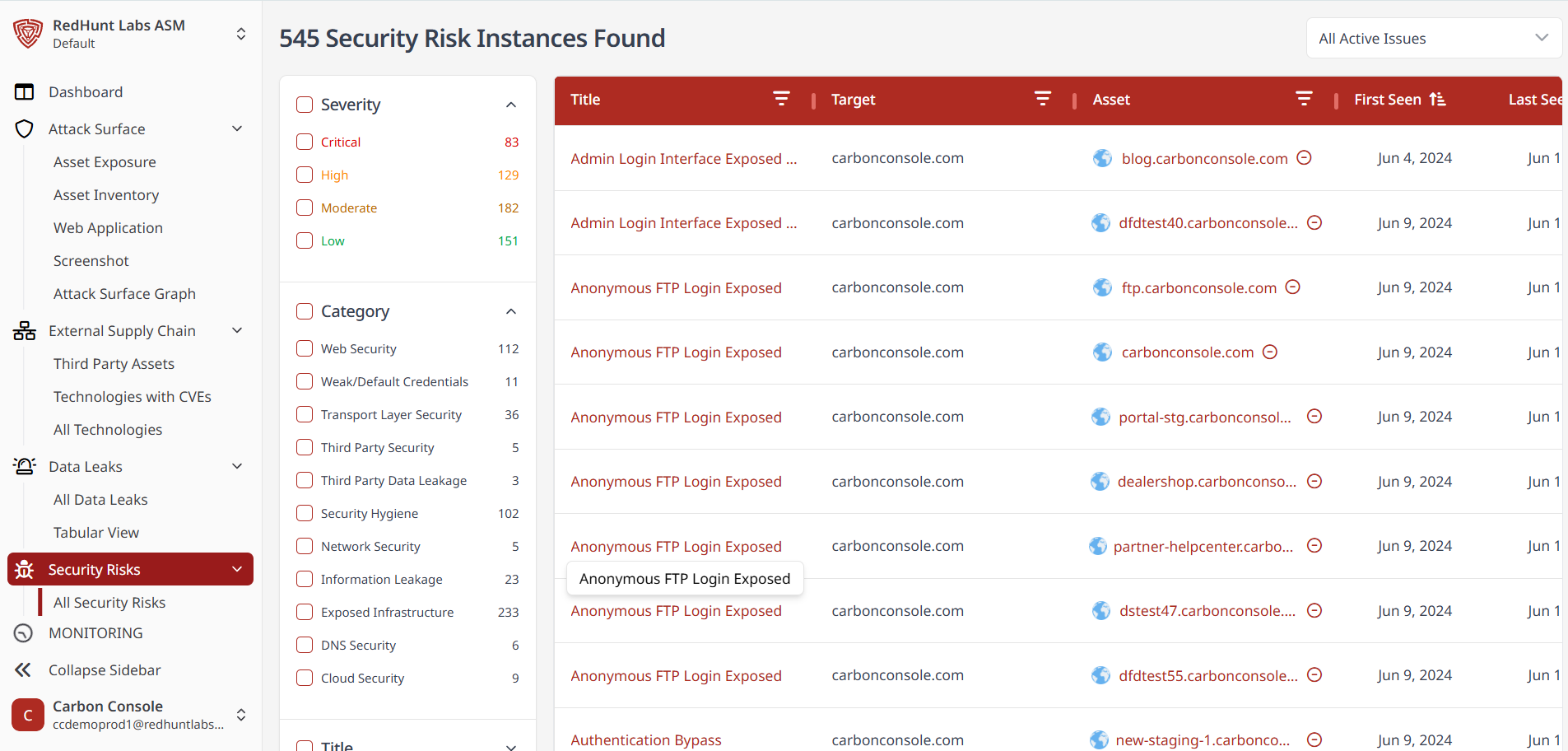
What Is a Severity Filter and How to Apply It?
- Security risk instances are classified by severity: Critical, High, Medium, and Low.
- These severity filters are located at the top left corner of the Security Risk screen.
- Click on a specific severity level to view all related risk instances under that category.
What Is a Title/Category Filter and How to Apply It?
- The platform includes a set of predefined security risk categories based on the most common vulnerabilities.
- These category filters are listed on the left-hand side of the Security Risk screen.
- Click on a desired category to view all security risk instances classified under that category.
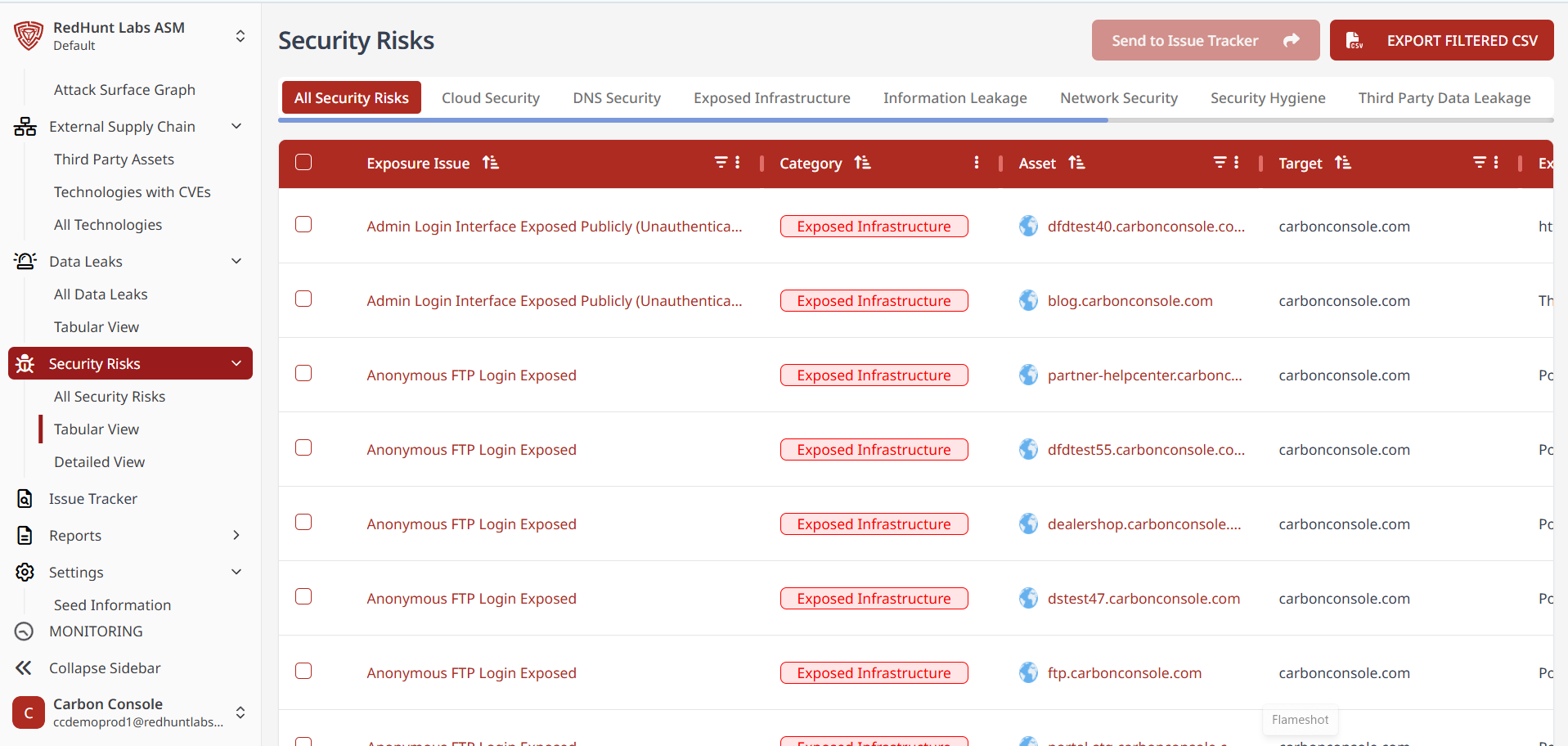
Features Available Under the ‘Tabular View’
- The Tabular View displays security risks in a structured row-and-column format, offering a more analyst-friendly interface.
- Both list and table layouts show the same core information, but the tabular view includes additional exposure instance details such as:
- Port numbers
- Protocols
- Nature of the risk
- Reason for the risk
- You can select multiple instances via the checkboxes on the left to send them to the issue tracker.
- Filters available:
- Asset (Asset URL)
- Exposure Issue (Security Risk Category)
- Clicking on an exposure issue will redirect you to the detailed view of that category.
Information Provided Under the Detailed View of Security Risks
Each predefined security risk category is explained in detail in the Detailed View section. Categories are accessible via the list on the left-hand side of the screen.
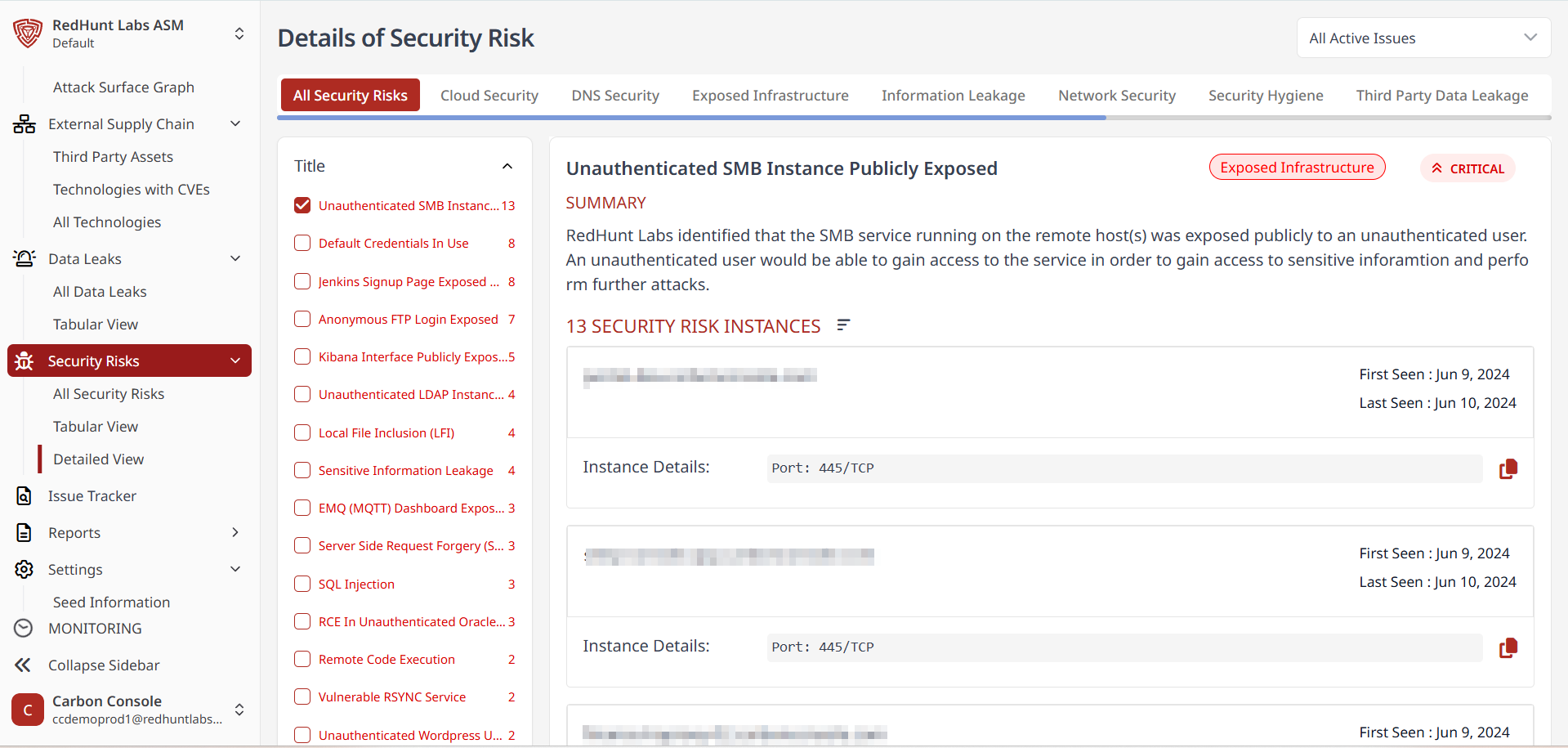
Each category includes:
- Summary: Description of the security risk
- Recommendation: Suggested fixes and best practices
- Reference: External resources for additional reading